A new point-of-sale (PoS) malware, called Punkey and affecting at least 75 terminals, has been identified to have evolved from NewPoSThings, a threat first spotted in September 2014 by Arbor Networks and believed to be under active development since at least October 2013.
The discovery was made during an investigation in collaboration with the US Secret Service, and despite source code similarities between the two malware pieces, security researchers at TrustWave found sufficient evidence to categorize Punkey under a separate PoS threat family.
Keylogging capabilities included
During the investigation, researchers uncovered three versions of the malware, although other builds may also be in use.
PoS malware is used by cybercriminals to pilfer payment card data from processing machines by extracting the sensitive financial information from the processes loaded in the memory of the system. This activity is called RAM-scraping.
It is believed that Punkey reaches a target system by leveraging weak passwords set up for remote administration of the payment processing terminals or by tricking checkout operators into opening malicious websites and/or emails straight from the PoS system.
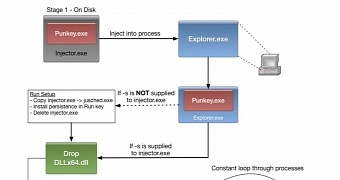
Once it is executed, the malware injects into the explorer.exe process to hide its presence and achieves persistence by creating registry startup entries.
Apart from the RAM-scraping capability, Punkey also includes a keylogging component that captures the keystrokes of the user in order to gather more credentials.
The task is achieved through a DLL (dynamic link library) called DLLx64, which is in fact a 32-bit DLL that can install and uninstall the window hooks for recording keyboard activity.
Unchanged encryption code used from online example
According to Trustwave researchers, Punkey is above the regular level of complexity seen in malware of the same type in that it resorts to hiding routines to avoid detection.
All the data extracted from the compromised system is encrypted then delivered to the remote command and control (C&C) server. Communication with the C&C is regular, unlike in the case of other PoS threats, allowing Punkey to download new variants of itself, or of other threats.
The encryption algorithm used to protect the traffic to the C&C is AES. According to Trustwave’s Eric Merritt, the analyzed versions rely on code available online, without any changes.
“The embedded keys match some example code and sure enough, after downloading and compiling a few changes I was successfully able to decrypt outgoing traffic,” Merritt writes in a blog post, adding that he wrote a decryption tool for the job.
One of the versions assessed has both 32-bit and 64-bit variants, but apart from being built for different architectures, they both have the same capabilities.
The researchers think that the source code similarities between Punkey and NewPoSThings may be the result of multiple actors having access to it or because the malware is customized for different operations.
 14 DAY TRIAL //
14 DAY TRIAL //