Results from sinkholing some command and control servers used by the Volatile Cedar cyber espionage operation reveal that most of the victims are based in Lebanon.
Check Point released on Tuesday a detailed report regarding the activity of a cyber-espionage campaign they dubbed Volatile Cedar conducted by attackers operating from Lebanon.
The operation has been active since late 2012 and managed to fly under the radar of antivirus solutions by deploying a new version of the malware, called Explosion by the researchers, used to infect computers and exfiltrate sensitive information.
In the technical analysis report, the experts say that some of the confirmed targets are entities that can be associated with organizations related to Israel and that others are based in Lebanon.
In total, live infections from 10 countries have been observed, the US, Canada, UK and Turkey being on the list. Info from Kaspersky reveals that the malware also reached Russia.
Kaspersky catches rare version of Explosion
Security researchers from Kaspersky sinkholed some of the command and control (C&C) infrastructure that relied on DGA (domain name generation), a tactic used by Explosion to generate domains for C&C servers that can be contacted if the connection to hard-coded IPs and dynamic update servers fails.
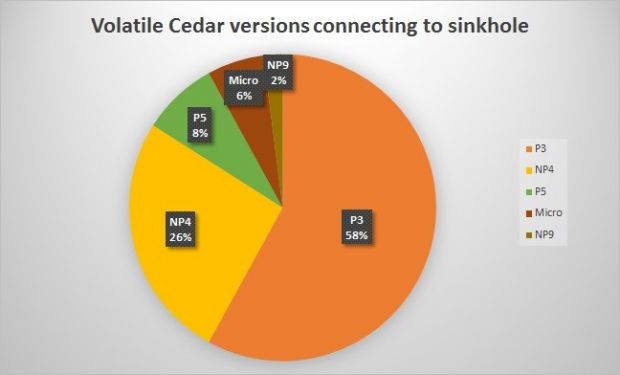
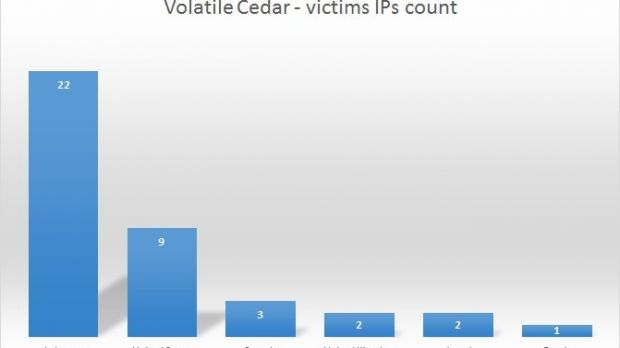
As per Kaspersky’s data, most of the infected machines trying to establish communication with an Explosion C&C are located in Lebanon, 22 unique IP addresses having been recorded.
Compromised systems from other countries have also been registered, 9 IPs being located in the US, 3 in Canada, 2 in United Kingdom and in Israel, and 1 in Russia.
“Clearly, the bulk of the victims we observe are all communicating from ip ranges maintained by ISPs in Lebanon. And most of the other checkins appear to be research related,” Kaspersky acknowledged in a blog post on Tuesday.
It is important to note that Check Point has also sinkholed C&Cs employed by Explosion malware, so the data provided by Kaspersky is partial.
Aside from this, the sinkhole received traffic (6%) from computers infected with an old version of the threat, Micro, which is considered to be “an early ancestor of the Explosive Trojan” from which all other four Explosion versions were spawned, and a very rare variant.
 14 DAY TRIAL //
14 DAY TRIAL //