Cybercriminals have created a piece of malware designed for Android that can go around protection features such as Advice of Charge (AoC) and Captcha to subscribe the user to premium-rate services.
The Trojan was spotted in 2014 but security researchers noticed that it was still under development. In early 2015, the threat was observed to be fully functional.
The AoC system is designed to alert users of applicable charges before subscribing to a service and requires explicit authorization.
Malware distributed mainly through VK social network
Detected by Kaspersky products as Trojan-SMS.AndroidOS.Podec, the malware is delivered mainly through social networks (Russia’s VK in particular) and it was observed to impact users in Russia and the neighboring countries (Kazakhstan, Ukraine, Belarus, Kyrgyzstan).
It appears that the cybercriminals disguise it as a cracked game (such as Minecraft Pocket Edition) or popular apps, which can be downloaded from unofficial Android app repositories.
Security researchers have discovered that the malicious program is promoted by several groups on VK social network, all of them sharing links to fake websites and relying on black SEO to make the content easier to discover.
“These groups have a lot in common: the way in which they are managed and designed (e.g. using keywords in place of descriptions, an abundance of simple broad-language messages characteristic of bots, etc.), the links they host to fake sites that seem to be copies of one idea. This suggests that black SEO (Search Engine Optimization) specialists were involved in distributing the Trojan,” the researchers say in a blog post on Wednesday.
Further investigation has revealed that the communities are under the administration of a user identified as “kminetti,” who created an account on October 12, 2011, and started to publish links to malicious sites and mobile apps in 2012.
Extensive functionality
Podec is aggressive during the installation procedure as it asks for administrative privileges, and if the request is denied, it keeps reiterating the demand, blocking the use of the device until its condition is met.
Furthermore, if the user tries to deny the escalated privilege, the screen is locked and the device restarts. Upon reboot, Podec still has the admin rights.
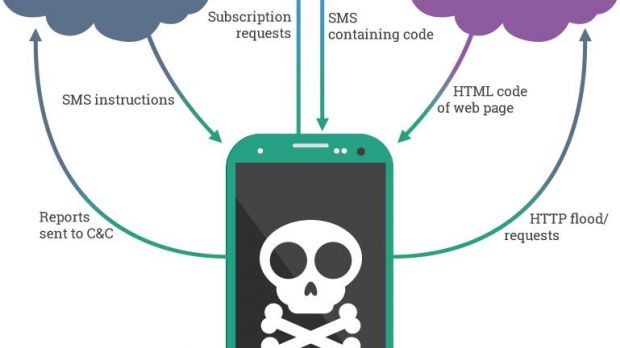
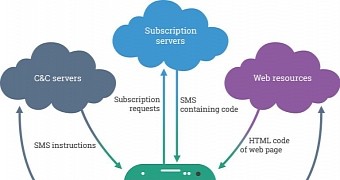
The malware’s functions include collecting data about the device (carrier, IMEI, phone number, language, country and city), enumerating the installed apps, sending SMS, filtering incoming messages, pushing ads or deleting messages and call records.
Additionally, it can also upload the source code of an HTML page to the command and control server, conduct DDoS attacks, subscribe to premium-rate services or initiate calls.
The researchers have also discovered that the operators of Podec can instruct it to exfiltrate certain messages from the device and delete installed apps.
Outsourcing Captcha decoding
However, the most interesting feature is bypassing Captcha security gates. According to Kaspersky’s analysis, this is achieved through the service provided by Antigate.com, which provides real-time Captcha-to-text decodings.
An image with the Captcha content is uploaded to Antigate and in a few seconds’ time an answer is delivered via text.
“In other words, the text from the CAPTCHA image is recognized by a person working for this service. According to the information Antigate.com provides on its website, most of its workers are based in India,” the researchers say.
By resorting to this method, the malware can subscribe the user to various online services automatically, without any human intervention.
Kaspersky analysts say that the malware showed signs that some functions are still to be implemented. One of them is “isRooted(),” which verifies if super-user privileges are available on the device.
However, this is not integrated in the main code of the malware, which suggests that payloads may be developed in the future to extend its functionality.
 14 DAY TRIAL //
14 DAY TRIAL //