The geographic distribution of industrial control systems (ICS) that can be accessed over the Internet has been published as a result of a research presented in October at the 4SICS (Security in Industrial Control Systems) in Stockholm.
ICS are machines used in industrial production, essential for critical infrastructure touching on sectors such as energy, water, oil, gas or data.
Due to their sensitive purpose, they should not be available over the web, especially since cyber espionage campaigns are constantly targeting them.
Attackers of ICS can better prepare their assault operation
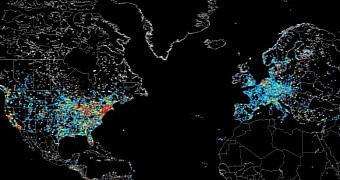
However, John Matherly, founder of Shodan, a search engine for Internet-facing devices, found that many ICS machines could be managed via a remote connection and created a map with these systems, drawing attention to the increased cyber attack risk they’re exposed to.
The map provides the location of all types of control systems, including machines in power plants. “You'd be surprised! A lot of big industrial stuff that you wouldn't expect to find on the Internet is being put online. And the problem is only getting worse as more people expect to be able to manage their business from their iPad,” he said.
Although from a security standpoint this practice should be avoided, saving time and money with maintaining the infrastructure seems to prevail, as technicians no longer have to take a trip to the location of the machine.
There is nothing wrong with setting up a remote connection in order to solve some computer problem with an ICS, but there are ways to make those machines invisible on the Internet, thus hiding them from the eye of an attacker.
Any information about a target is useful, more so in the case of cyber espionage, and learning about the infrastructure of the victim helps hackers determine flaws that can be exploited.
Patching ICS already takes a long time
It is a known fact that industrial control systems are more difficult to update because a certain maintenance schedule has to be respected to minimize any impact on the production. On the same note, software developers for these systems cannot always integrate a patch immediately after a vulnerability has been closed.
An example is the recently updated distributed control system from Siemens, SIMATIC PCS7 (distributed control system), whose built-in WinCC was known to be vulnerable before July, when it received a fix. However, the patch for the PCS7 came with the new release, on October 23.
Simatic WinCC is a SCADA (supervisory control and data acquisition) and human-machine interface (HMI) system that can monitor and control the physical processes in industrial control systems on a large scale.
Attacks on ICS happen frequently, and sometimes the software threats used can persists for years, as it was revealed in an alert from the US ICS-CERT on Wednesday, where an ongoing campaign leveraging BlackEnergy malware was discovered to have started since 2011.
 14 DAY TRIAL //
14 DAY TRIAL //