A campaign involving multiple WordPress websites has been discovered by security researchers to deliver several types of threats, from malware droppers to Trojans.
WordPress websites are a general target for cybercriminals, as most of the times their administrators lack the necessary technical skills, or the interest, to maintain the online location safe and sound.
Websites used as drop points by exploit kit authors or spammers
There are more than 50 websites compromised and the subject of interest they cater for does not follow a specific pattern. However, they do have something in common and that is the fact that the URLs include the “/1.php?r” string.
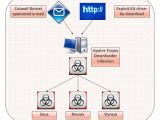
The researchers at Zscaler believe that the compromised online locations are used by authors of exploit kits as drop sites for malware. According to them, email spam could also be used for delivering the threats to the victim.
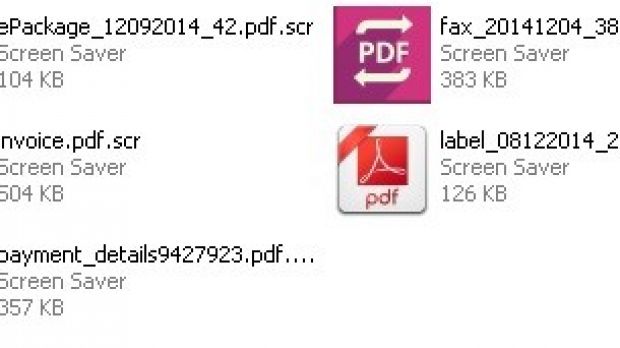
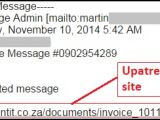
A message containing a link to one of these websites could trick the recipient into believing that they have been directed to download an invoice or a document of some kind that requires urgent attention.
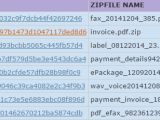
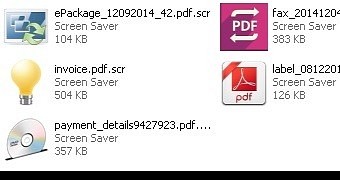
The reason this theory is plausible is that the researchers noticed that all malware samples were archived and most of the ZIPs claimed to contain a PDF file. Extracting the content showed that it was actually an executable item with a double extension to deceive the user into launching it.
Detection of the samples is poor
Among the threats observed by the security experts there was Upatre, a malware dropper that has been associated with multiple botnets, including Asprox.
Another one is Hencitor, which is also employed to funnel in other malware, created for different tasks.
Zscaler also informs that Vawtrak, a banking Trojan also known as Neverquest, has also been spotted. This malware is under active development at the moment and its authors have recently implemented new functionality.
Extrat Xtreme RAT is on the list of distributed malware, too. This is a remote access Trojan designed to steal stored passwords, run commands on the affected system, log webcam data and keystrokes, as well as exfiltrate the information to a server under the control of the attacker.
A worrying fact is that Zscaler checked the detection rate for the samples they found and the results were far from cheerful.
“Such campaigns generally drop variants of well-known malware families, which are undetected by the AV vendors. By the time of analysis we observed poor detection rates for the malware samples involved in this campaign,” Rubin Azad says in a blog post.
 14 DAY TRIAL //
14 DAY TRIAL //