Cybercriminals seem to have learned a new method to bypass anti-spam filters, by delivering email with an empty Word document in the attachment, security researchers say.
The lure to open the file is far from being an uncommon one: a document pretending to relay financial information of some sort (invoice, bank statement, bill); however, it carries absolutely no information except for the malicious payload under the form of macros.
Ransomware could be delivered to potential victims
The macro feature is used in Office components to help the user go through repetitive tasks in an automated manner by executing a sequence of predefined commands.
Malware authors have seen the potential of the option and started to embed malicious commands that would trigger the download and execution of a threat on the user’s computer.
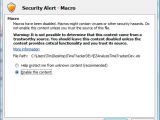
Out of caution, Microsoft made the feature inactive by default, offering customers who needed it the possibility to enable it. Furthermore, upon turning macros on, a message informs the user of the associated risks.
Security researchers at Bitdefender have detected a spam campaign that relies on documents with malicious macros to deliver malware from a remote location. The malware could be of the ransomware type or any other kind of threat, since the antivirus vendor did not make it clear.
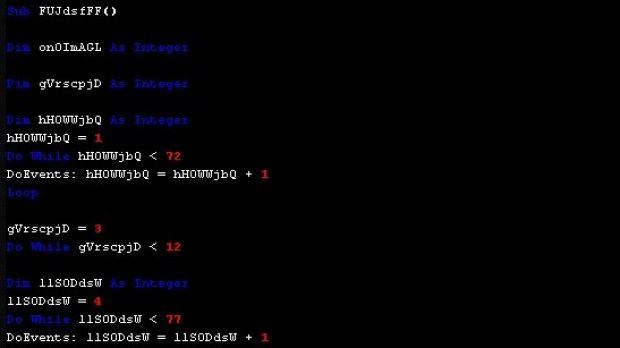
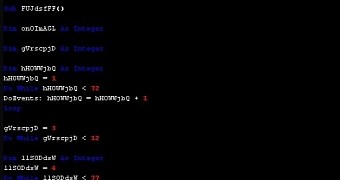
Macro code is obfuscated to evade detection
In most cases, the anti-spam protection available on the email server would prevent potentially dangerous messages from reaching the inbox folder, but the researchers say that in this case, because the document does not contain any text, the email is no longer stopped.
Bitdefender says that the macro code is obfuscated to bypass traditional antiviruses, which means that the malicious message is capable of getting past another layer of defense.
It appears that this spam campaign had no less than 7,000 emails delivered in one day, mostly to users in Italy, France, US, UK, Australia, Canada and Germany.
Avoiding infection is quite simple and consists in keeping the macro feature disabled. When the malicious document is opened, a security alert pops up informing of the potential risk; just cancel the pop-up and the command for downloading the malware won’t be initiated.
 14 DAY TRIAL //
14 DAY TRIAL //