There’s an ever-growing feud between book lovers – the choice between paper and electronic seems to split people into groups. These days, however, you should probably be a little more careful if you’ve adopted the latter.
It seems that there’s a bug going around, making rounds attached to e-books that can hack people’s Amazon accounts.
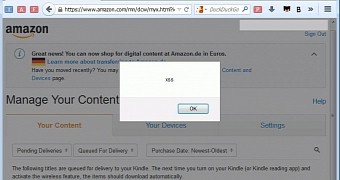
A security researcher has discovered a security hole in the “Manage your Kindle page” on Amazon’s website that provides hackers with the needed data – users’ credentials. This happens when you upload a malicious e-book to your account and move it through Amazon’s system to store it on your device.
The Send to Kindle plugin for Windows and Mac can be used to send personal documents to Kindle, including e-books from other sources than Amazon. These end up archived in the Kindle Library in the cloud and they can be downloaded to the connected devices at any time, be them Kindles or mobile devices with the Kindle app, or even the desktop app.
If one of the e-books you put on your device has been hacked to include a script in the title, then you could easily see your Amazon account in trouble, along with all your data. The code is executed once the book that was added to the library is opened in a web page. Hackers can then access the cookies related to Amazon and take over the account.
The bug was fixed nearly a year ago, but has made a comeback
Researcher Benjamin Mussler states that he first discovered the flaw nearly a year ago and reported it to Amazon. While the issue was fixed at the time, it seems that the problem is still very much present and that it has made its way into the new “Manage Your Kindle” page.
“When I first reported this vulnerability to Amazon in November 2013, my initial Proof of Concept, a MOBI e-book with a title similar to the one mentioned above, contained code to collect cookies and send them to me. Interestingly, Amazon's Information Security team continued to use this PoC on internal preproduction systems for months after the vulnerability had been fixed. This made it even more surprising that, when rolling out a new version of the ’Manage your Kindle’ web application, Amazon reintroduced this very vulnerability,” he wrote on the issue.
He adds that the issue goes farther than Amazon though. Calibre was also affected by the same bug last year, but seems to have fixed it in the meantime.
 14 DAY TRIAL //
14 DAY TRIAL //